Overview
DHCP snooping feature ensures that DHCP clients obtain IP addresses from legitimate DHCP servers only, and records the correspondence between IP addresses and MAC addresses of DHCP clients to prevent DHCP attacks on the network. It is one of the security features introduced on the GWN78xx network switches.
To ensure the security of network communication services, the DHCP Snooping technology is introduced, and a firewall is established between the DHCP Client and the DHCP Server to defend against various attacks that can present high-security risks, and to make sure that only the trusted interface can have an established connection to the DHCP server which is in most cases: A router device.
How DHCP Snooping Works
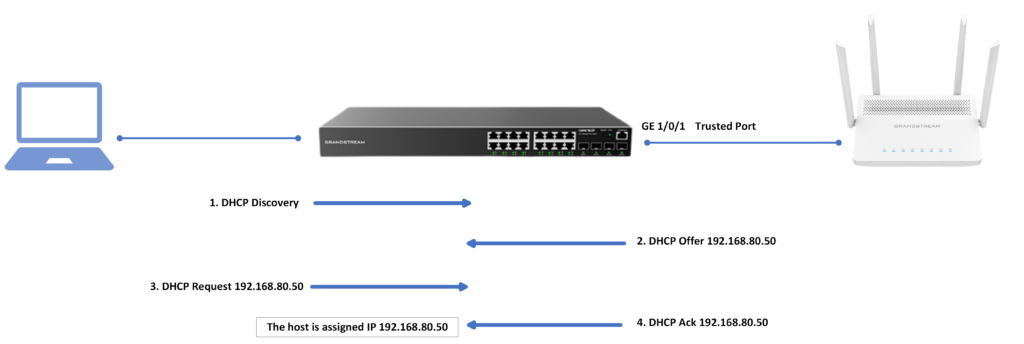
A device with DHCP snooping enabled sends DHCP request packets from users ( DHCP clients) to a valid DHCP server through a trusted interface. The device generates a DHCP snooping binding table according to the DHCP ACK message returned by the DHCP server. Afterward, when the device receives DHCP packets sent by users from the DHCP snooping-enabled interface, it will perform a matching check, which can effectively prevent attacks from illegal users.
Important Parameters
Please refer to the below definitions in case needed, as we will be configuring them in the upcoming example:
- DHCP Option 82
The DHCP option 82 records the location information of the DHCP Client. By adding Option 82 in the DHCP request message, the precise physical location information of the DHCP client is passed to the DHCP server, so that the DHCP server can assign the appropriate IP address and other configuration information to the host, and realize the security control of the client.
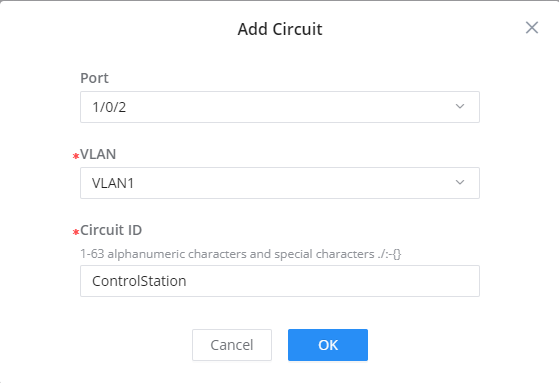
- Circuit ID
Mainly used to identify the VLAN, the interface on which the client is connected, and other information such as its location.
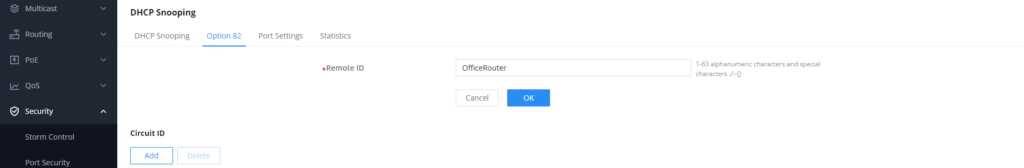
- Remote ID
Mainly used to identify the device accessed by the client, generally The MAC address of the device.
- Chaddr Verification
This is to check whether the source MAC address of the reported DHCP message frame header is the same as the Chaddr field. It is disabled by default.
- Rate (pps)
If and only when the trust mode is turned off, the speed limit function will take effect. It sets the rate of the port DHCP packet processing unit, ranging from 0 to 300. 0 means no rate limit, and the default is 0. After the setting is completed, if the actual rate exceeds the maximum allowed rate, the port will be error-down.
- Option 82 Mode
This parameter provides information about what the GWN78xx switch does with received packets from the DHCP server, that contain DHCP option 82 information, the three options are: Drop, Keep, or Replace:
- Keep: If the packet contains Option 82, keep Option 82 in the packet unchanged and forward it.
- Drop: If the packet contains Option 82, the packet will be discarded directly.
- Replace: If the packet contains Option 82, the original Option 82 in the packet will be replaced and forwarded.
Configuration Example
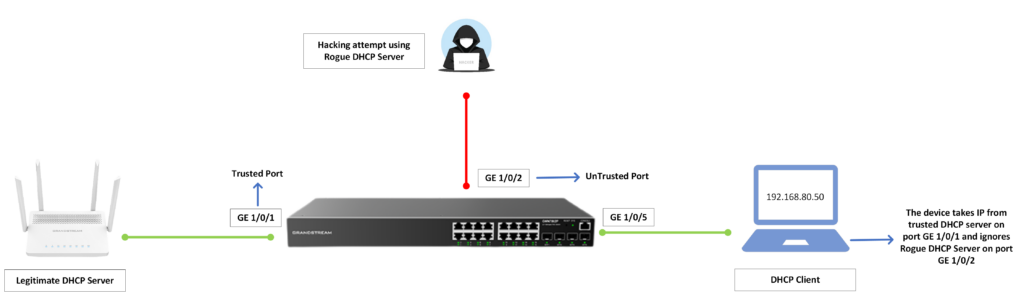
Let’s consider the following scenario, we are deploying a GWN78xx switch in our office as a distribution switch, the switch will be connected directly to our internet gateway and DHCP server, which is a GWN7062 router.
To take further security measures, we want to make sure that our router is the only DHCP server that will be defined on our network, which means there will be no other devices connected to the switch that will be able to assign IP addresses to connected clients.
The topology below illustrates the case scenario:
To perform the required actions, please follow the below steps:
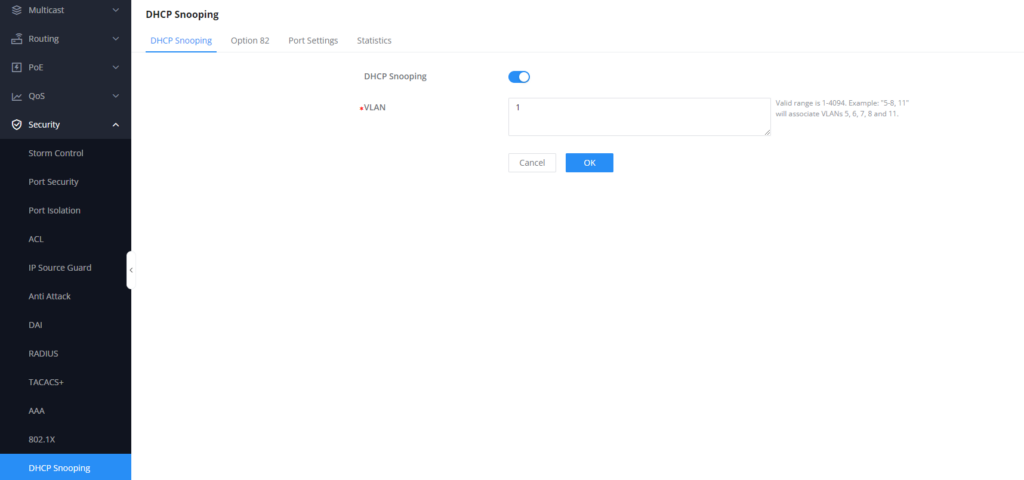
- Access the switch’s Web UI and go to Security → DHCP Snooping, Enable it, and Select VLAN 1 (Default VLAN)
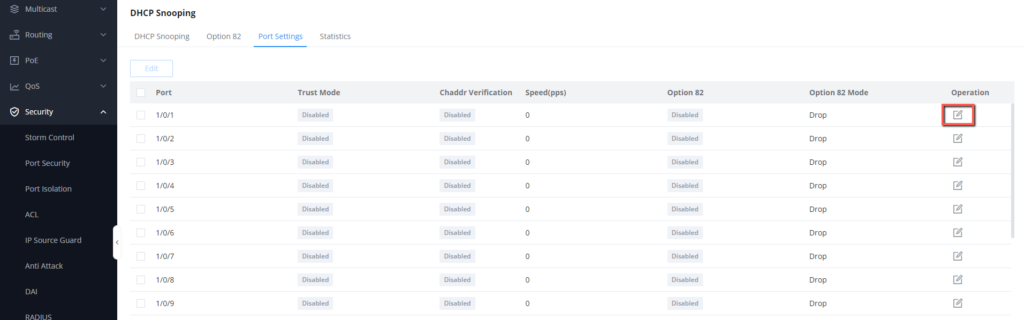
- Identify the port on which the DCHP server ( Router ) will be connected.
- Under Security → DHCP Snooping → Port settings, select the port (GE 1/0/1)
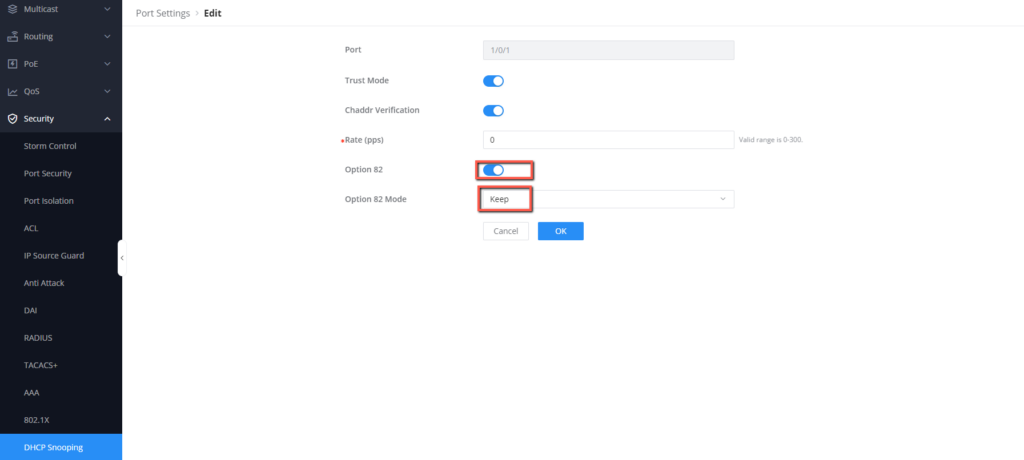
- Enable Trust Mode and Chaddr Verification.
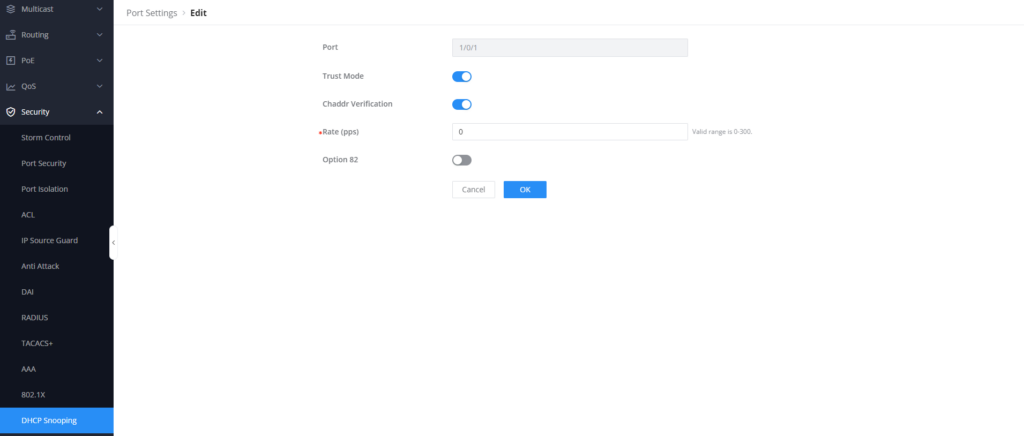
- Enable Option 82 to provide more information about the connected DHCP server and its location,
- Set Option 82 Mode to “Keep”, click OK, then save the configuration.
- Go to Security → DHCP Snooping → Option 82, Define Remote ID to be “Office Router”
- Add Circuit ID in case you want to specify the location and interface of the connected clients, for informational purposes, we will add a circuit ID for a connected control station, that will be connected to port 1/0/2.
The results are: the GWN78xx will only accept DHCP ACK messages received from the DHCP server connected on port 1/0/1, any other interface where a DHCP server is connected will be discarded.
If we attempt to connect another DHCP server on a different port other than the 1/0/1 port, it will not be able to assign IP Addresses as it is not connected to a trusted port.
Supported Devices
Device Name | Supported | Firmware Required |
GWN7801 | Yes | 1.0.3.19 or higher |
GWN7801P | Yes | 1.0.3.19 or higher |
GWN7802 | Yes | 1.0.3.19 or higher |
GWN7802P | Yes | 1.0.3.19 or higher |
GWN7803 | Yes | 1.0.3.19 or higher |
GWN7803P | Yes | 1.0.3.19 or higher |
GWN7811 | Yes | 1.0.1.8 or higher |
GWN7811P | Yes | 1.0.1.8 or higher |
GWN7812P | Yes | 1.0.1.8 or higher |
GWN7813 | Yes | 1.0.1.8 or higher |
GWN7813P | Yes | 1.0.1.8 or higher |
GWN7806 | Yes | 1.0.1.14 or higher |
GWN7806P | Yes | 1.0.1.14 or higher |
GWN7816 | Yes | 1.0.3.8 or higher |
GWN7816P | Yes | 1.0.3.8 or higher |
GWN7830 | Yes | 1.0.3.3 or higher |
GWN7831 | Yes | 1.0.3.3 or higher |
GWN7832 | Yes | 1.0.3.3 or higher |
List of supported devices