Overview
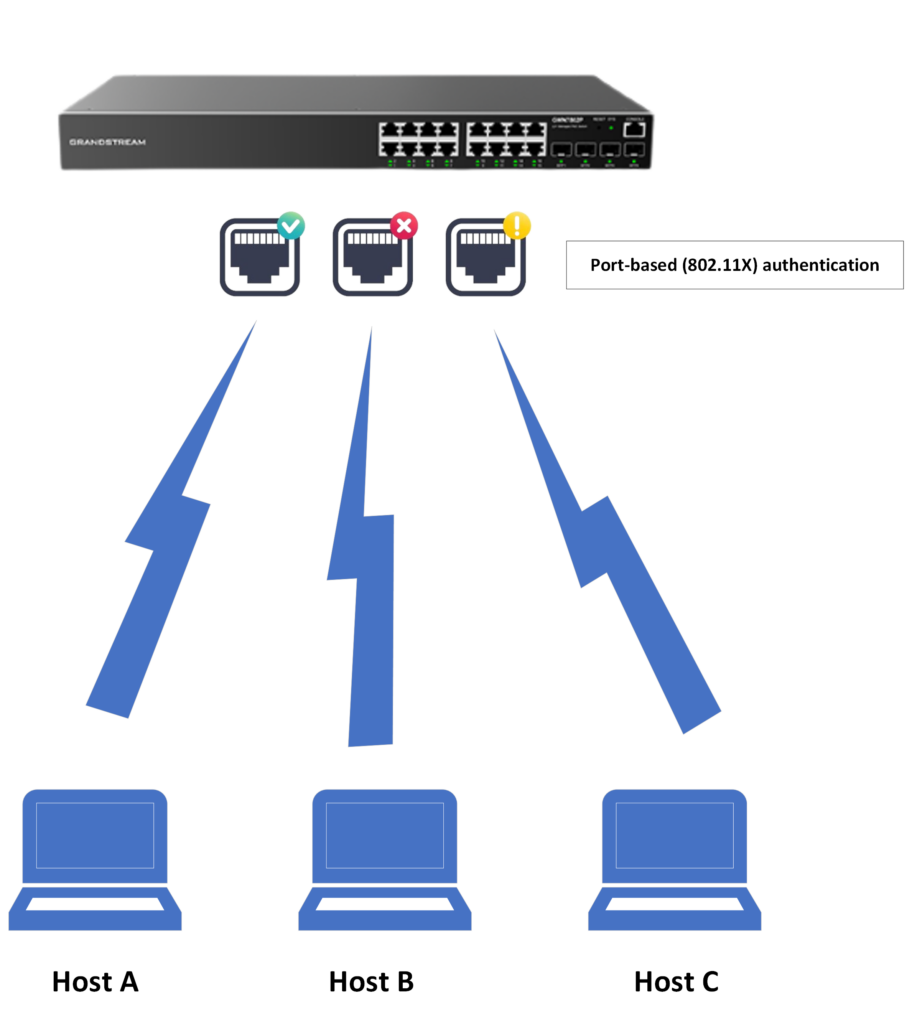
Network access control (NAC) is a security feature that allows network administrators to monitor and record the sessions registered on the GWN78xx, this helps to give a broader image of the type of devices connected to the network through the GWN78xx network switch and allows only the ones that can authenticate with a radius server, this type of authentication is called port-based authentication, also know as 802.1X authentication, because each port of the switch will have its separate type of authentication than the other.
NAC authentication methods
The below table compares some of the differences between the authentication methods that the GWN78xx switch uses to grant or deny access to the network, these mechanisms can work simultaneously, with other security implementations such as an access control list, AAA…
Feature | Port-Based (802.1X) Authentication | MAC Authentication | Portal Authentication (Web Authentication) |
Authentication Method | Username/password | MAC address | Username/password |
Security Level | High | Moderate | Low |
Granularity of Control | High (Per-user/device policies) | Low (Device-specific control) | Limited |
Complexity of Setup | Moderate to High | Low | Low |
Ease of Use | Requires supplicant | Simple setup | User interaction required |
Scalability | Scalable for large networks | Scalable | Suitable for smaller networks |
Spoofing Concerns | Low (Depends on chosen methods) | Moderate (MAC addresses spoofable) | Low (Username/password can be shared) |
Supported Devices | Requires supplicant support | Works with most devices | Works with any device with a web browser |
Use Cases | Enterprise networks | Basic access control | Guest networks, public hotspots |
Layered Security | Part of a layered security approach | Limited security | Often used as a supplementary method |
Some differences between the NAC authentication methods
NAC and AAA cooperate to complete the access authentication function together.
- NAC: It is used for the interaction between users and access devices. NAC is responsible for controlling the access mode of users, that is, which mode the user uses to access 802.1X, MAC, or Portal, and various parameters and parameters in the access process. timer. Ensure that legitimate users and access devices establish a secure and stable connection.
- AAA: used for the interaction between the access device and the authentication server. The AAA server controls the access rights of the access users by authenticating, authorizing, and accounting for the access users. for more information on how to configure AAA, please refer to the guide: GWN78xx – AAA Configuration
In this guide, our focus will be on the 802.1X authentication procedure, also known as port-based authentication, which is considered the most secure method for network access security.
Configuration Example
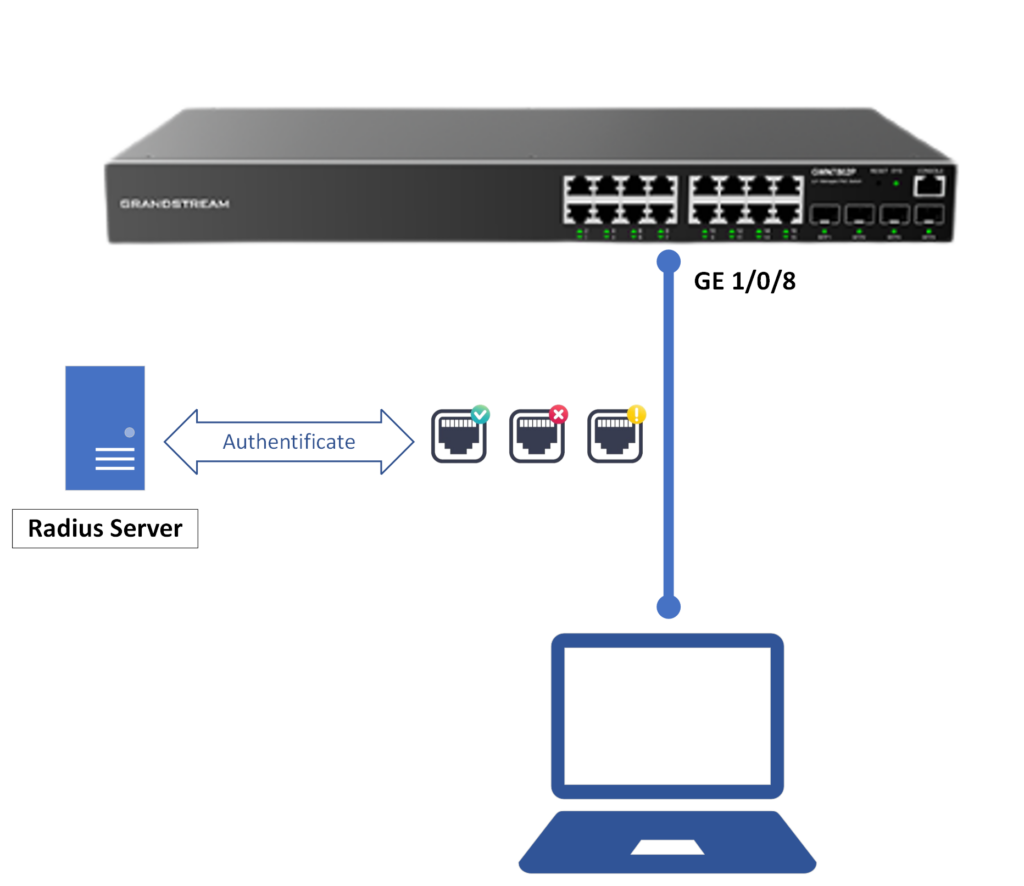
In our example we will be applying security measures to allow administrators to add devices to the network after entering the radius authentication only, this means that when a device is plugged on a specific GWN78xx switch port, it will require authentication for radius username and password in order to grant the device access to the network.
Consider the below scenario:
This displays connecting a laptop by RJ45 cable on port 1/0/8:
- In a normal scenario where NAC is not configured, the laptop will get an IP address from the network through GWN78xx with no issue.
- In the case where NAC is configured, a radius authentication will be required to allow the laptop to get an IP address from the network through the GWN78xx switch.
Let’s dive into the configuration of the second scenario:
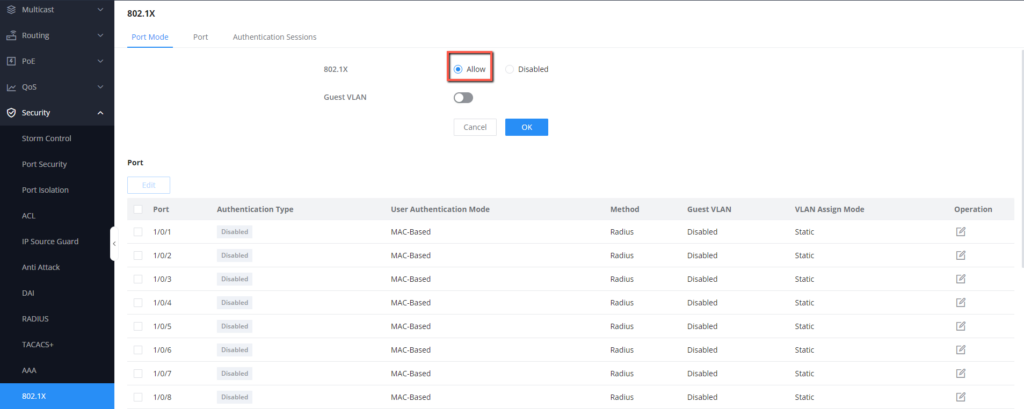
- On the GWN78xx Web UI, Go to Security → 802.1X → Port Mode
- Enable 802.1X Authentication, by setting it to allow
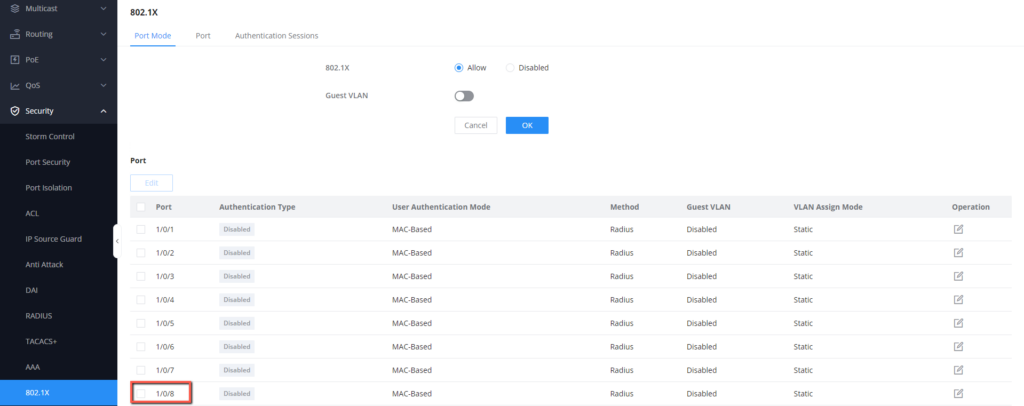
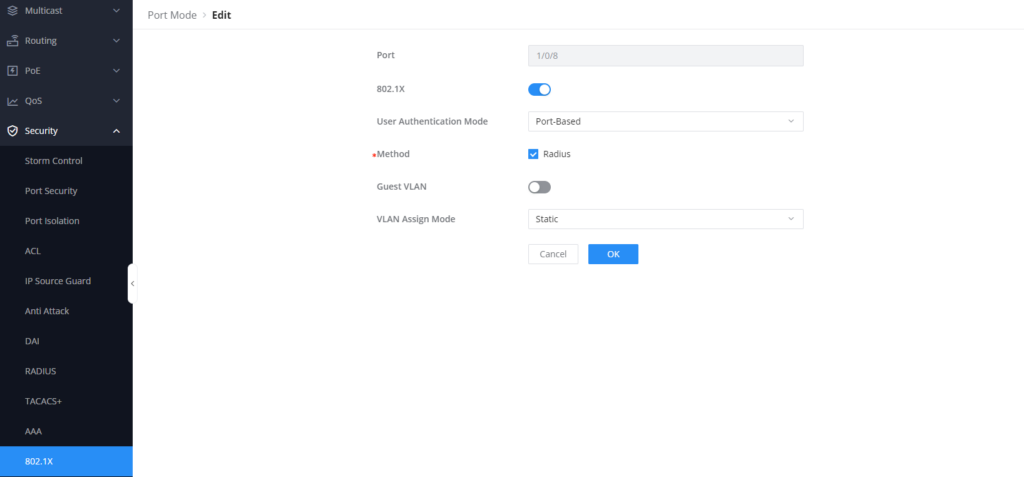
- Go to the specific port 1/0/8 and click on
to edit its parameters.
- Enable 802.1X on that specific port.
- Set User Authentication mode to Port-based, this is to allow multiple users to authenticate, and as long as one user passes the authentication, the rest of the users are exempt from authentication, to make that port explicit for that specific laptop. Click OK, then Save the settings
- The authentication method will use a Radius server, please refer to the AAA configuration guide for more information about how to set up your radius server locally,
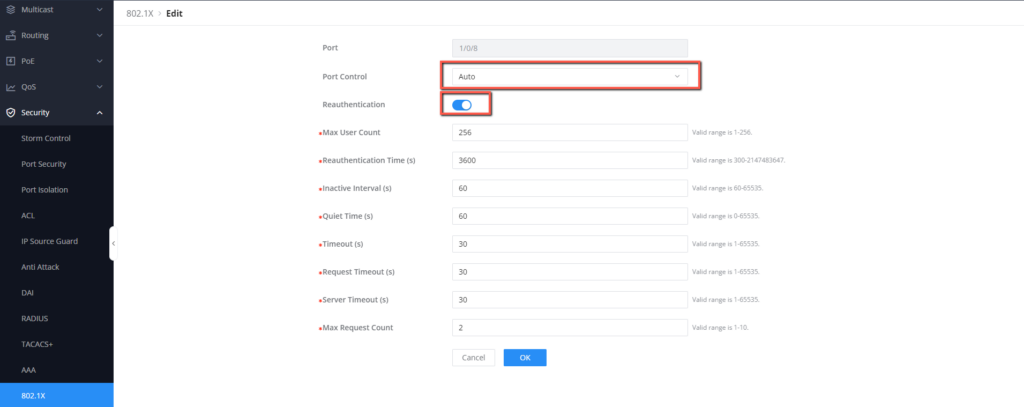
- Go to Security → 802.1X → Port, select port 1/0/8 ,
- Set the Port control to auto, and enable the re-authentication, to allow the port to authenticate the credentials provided with the credentials defined on the radius server.
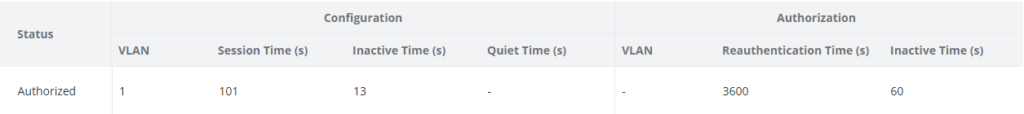
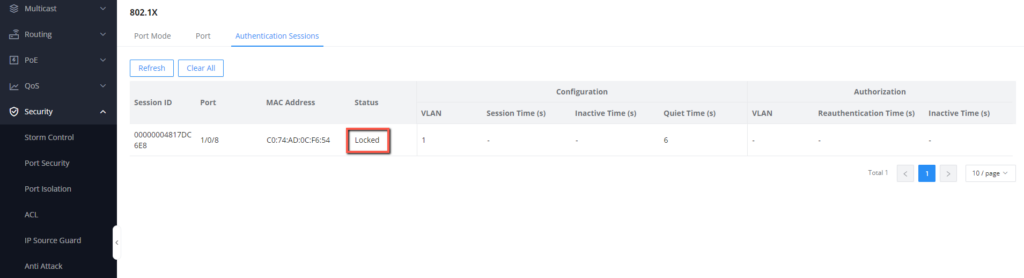
- If the authentication is not completed, the connected device will not have access to the network, and will be displayed under the list of authentication sessions, with its MAC address, the port on which it’s connected, and its status “locked”, as displayed below:
- Once the authentication is completed on the laptop by providing the radius credentials, then the access will be authorized and the device can now access the network.
Guest VLAN
The way Guest VLAN configuration works is simple, consider a scenario where we want to make sure that external devices that are connected to our network through the GWN78xx switch, are automatically moved into a VLAN dedicated only for external connections, we will call this VLAN a Guest VLAN, after a successful configuration, each connected device plugged will be set to be part of the guest VLAN defined. the steps for configuration are as follows:
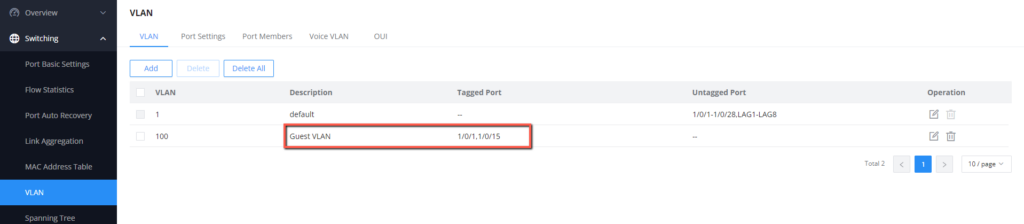
- Under Switching → VLAN, Create a Guest VLAN
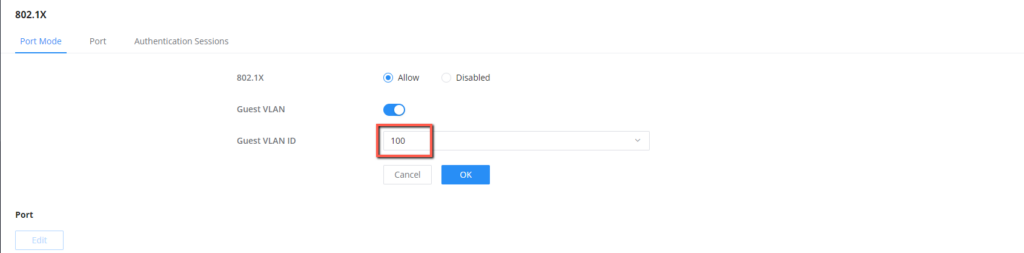
- Under Security → 802.1X → Port Mode, Enable Guest VLAN, and set the Guest VLAN ID to 100.
- Identify the port on which the external devices will be connected Eg. a Wireless Access Point that will give wireless connection to guest devices. it will be port 1/0/15 for our case
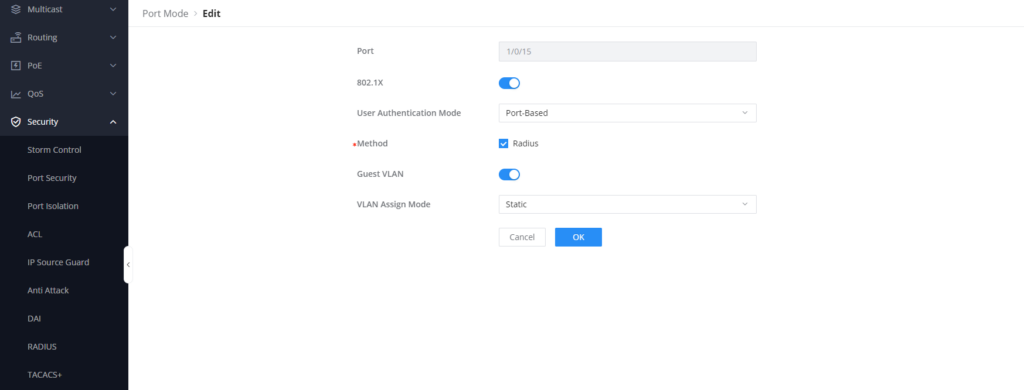
- On that specific port, enable 802.1X, set the user authentication mode to Port-Based,
- Enable Guest VLAN on that port, this will make the connected device be moved to the guest VLAN.
- The VLAN assign mode refers to how the switch handles VLAN assignment for clients that successfully authenticate using the 802.1X protocol, we will set it to static, which means a specific VLAN is statically assigned to the port for authenticated clients.
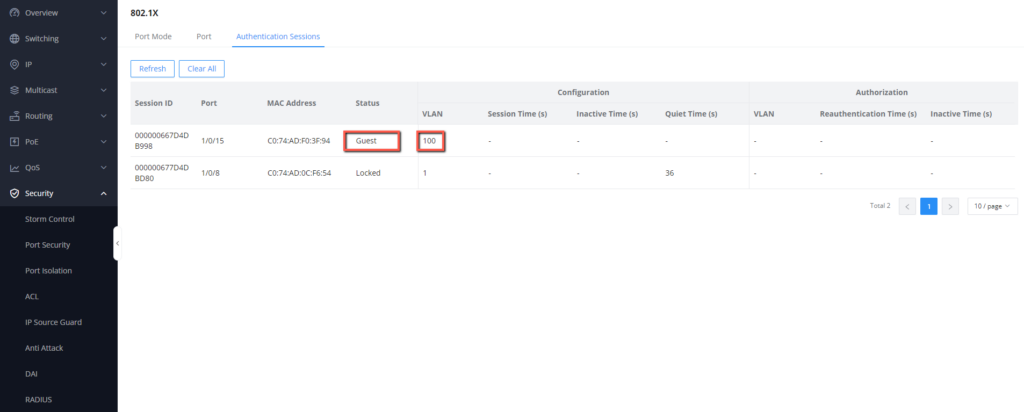
With this configuration, if we plug on port 1/0/15 a wireless access point that will be used for connecting external devices wirelessly, then it should be displayed as a guest device, with VLAN 100 on the authentication session table:
Supported devices
Device Name | Supported | Firmware Required |
GWN7801 | Yes | 1.0.3.19 or higher |
GWN7801P | Yes | 1.0.3.19 or higher |
GWN7802 | Yes | 1.0.3.19 or higher |
GWN7802P | Yes | 1.0.3.19 or higher |
GWN7803 | Yes | 1.0.3.19 or higher |
GWN7803P | Yes | 1.0.3.19 or higher |
GWN7811 | Yes | 1.0.1.8 or higher |
GWN7811P | Yes | 1.0.1.8 or higher |
GWN7812P | Yes | 1.0.1.8 or higher |
GWN7813 | Yes | 1.0.1.8 or higher |
GWN7813P | Yes | 1.0.1.8 or higher |
GWN7806 | Yes | 1.0.1.14 or higher |
GWN7806P | Yes | 1.0.1.14 or higher |
GWN7816 | Yes | 1.0.3.8 or higher |
GWN7816P | Yes | 1.0.3.8 or higher |
GWN7830 | Yes | 1.0.3.3 or higher |
GWN7831 | Yes | 1.0.3.3 or higher |
GWN7832 | Yes | 1.0.3.3 or higher |