The GWN Access Points offer the ability to prevent malicious intrusion to the network and increases the wireless security access of clients when introducing Rogue AP Detection feature.
A Rogue AP is an access point that has been installed on a secure network without explicit authorization from network administrators. Rogue access points can negatively impact the performance of wireless networks and pose a security threat because anyone with access to the premises can ignorantly or maliciously plug a wireless AP to the local network which can undermine the security of an enterprise network by potentially allowing unchallenged and unauthorized access.
In this guide, we will go through the configuration steps to enable the AP Rogue Detection feature on a GWN76xx access point.
ROGUE AP DETECTION CONFIGURATION
Configuration Steps
In the next sections, we provide the needed configuration steps to enable Rogue AP Detection feature on GWN access points:
Enabling Rogue AP Detection Feature
To enable the Rogue AP Detection feature, Access the GWN76xx web GUI, and navigate to “Security” →
“Rogue AP” → “Configuration” as shown in below screenshot.
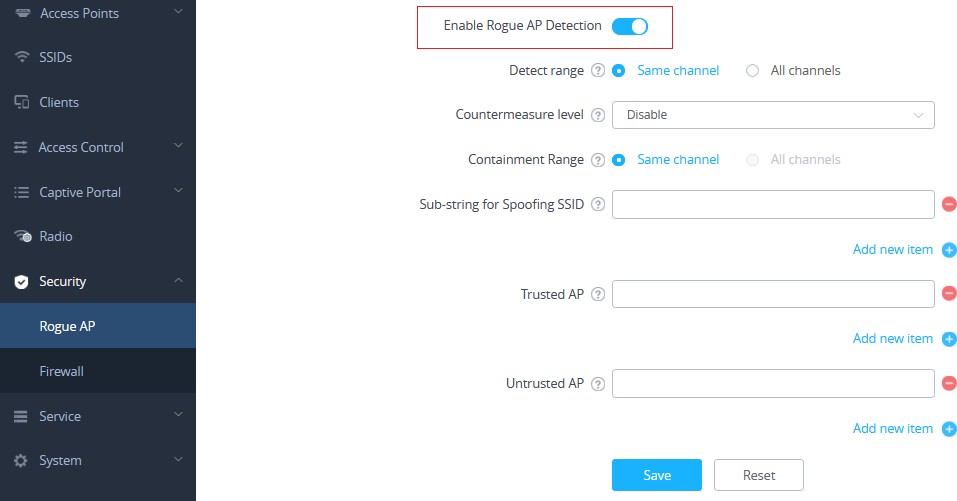
In below table you can find the description for the related parameters and options.
| Field | Description |
| Enable Rogue AP Detection | Select to either to enable or disable Rogue AP scan. |
| Detect range | Specify the Rogue AP detect range.
Default is Same channel. |
Countermeasure level | Countermeasures level specifies the type of attacks which will be suspected by the AP. Select different levels:
Default is Disabled. Notes:
|
Containment Range | Specify the containment range:
Default is Same channel. |
Sub-string for Spoofing SSID | The AP broadcasting SSID with the specified string will be classified as a Spoofing SSID. |
| Trusted AP | You can specify MAC address of the trusted AP, which should be formatted as XX:XX:XX:XX:XX:XX. If an AP is defined as trusted AP, no countermeasures will be executed on it. |
| Untrusted AP | You can specify MAC address of the untrusted AP, which should be formatted as XX:XX:XX:XX:XX:XX. If an AP is defined as untrusted AP, countermeasures will be executed on it when countermeasure is enabled. |
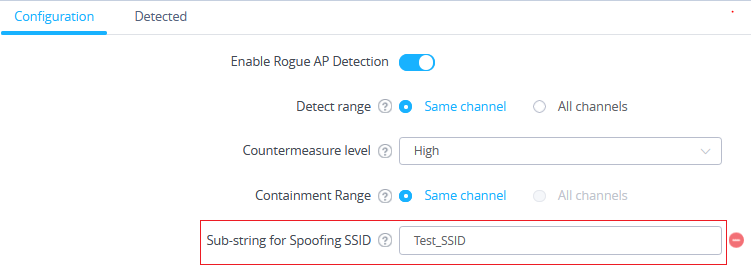
Adding the Spoofing SSID String
Users can specify an SSID string to be checked for potential rogue access points transmitting the same SSID, this is to prevent SSID spoofing rogue access points from masquerading the legitimate SSID broadcasted by GWN76xx. In the example from below screenshot we have added Test_SSID as the spoofing SSID string.
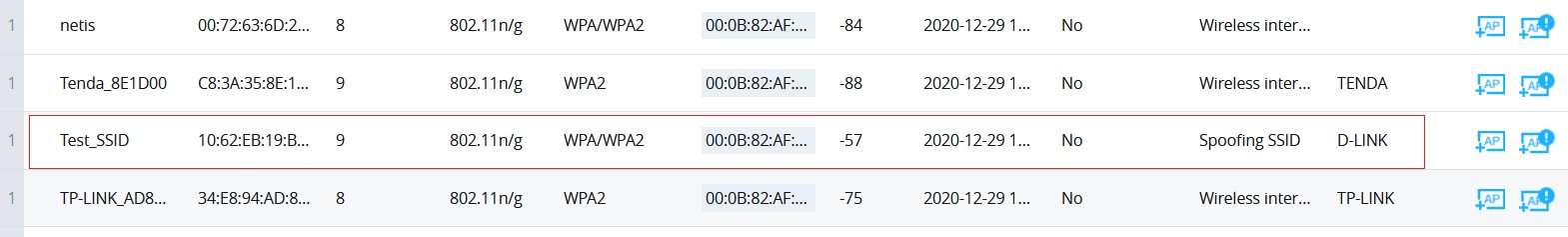
Once the GWN76xx detects an AP broadcasting the exact SSID string like in our example “Test_SSID”, it will be reported in the “Detected” page as “Spoofing SSID”, and if enabled a countermeasure to contain that AP could be taken from the GWN76xx AP to prevent wireless clients from associating with that SSID.
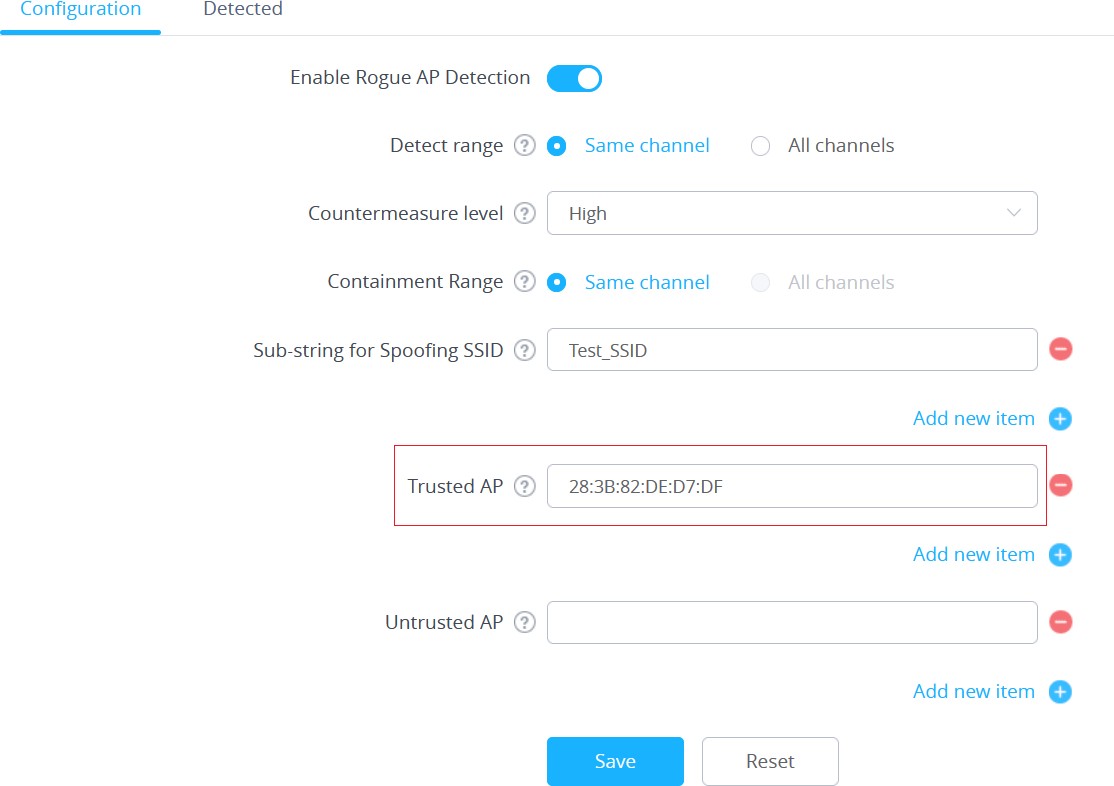
Adding Trusted AP
Users can add trusted access points by specifying their MAC addresses under “Security” → “Rogue AP” → “Configuration”
You can also define an AP as trusted from the “Actions” tab located under “Security” → “Rogue AP” → “Detected” by clicking the icon as shown in below screenshot.
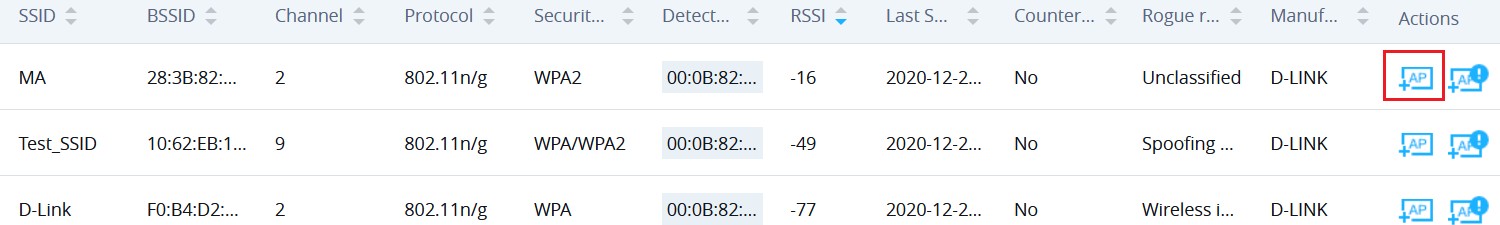
Once an AP is added as trusted, it will be displayed under “Detected” page as “Trusted AP”
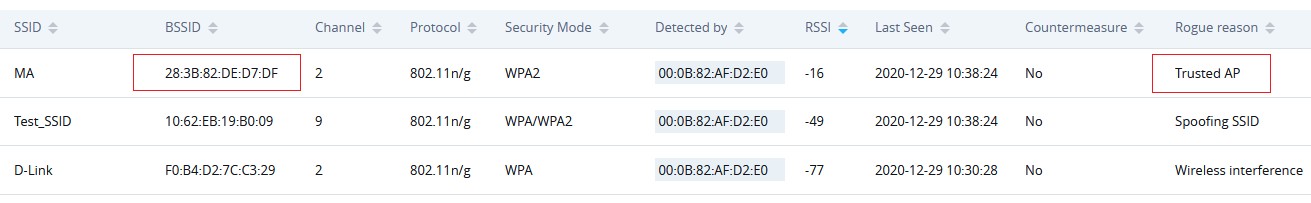
Note: If an AP is defined as trusted AP, no countermeasures will be executed on it when countermeasure is enabled.
Adding Untrusted AP
Users can add Untrusted access points by specifying their MAC addresses under “Security” → “Rogue AP” → “Configuration”.
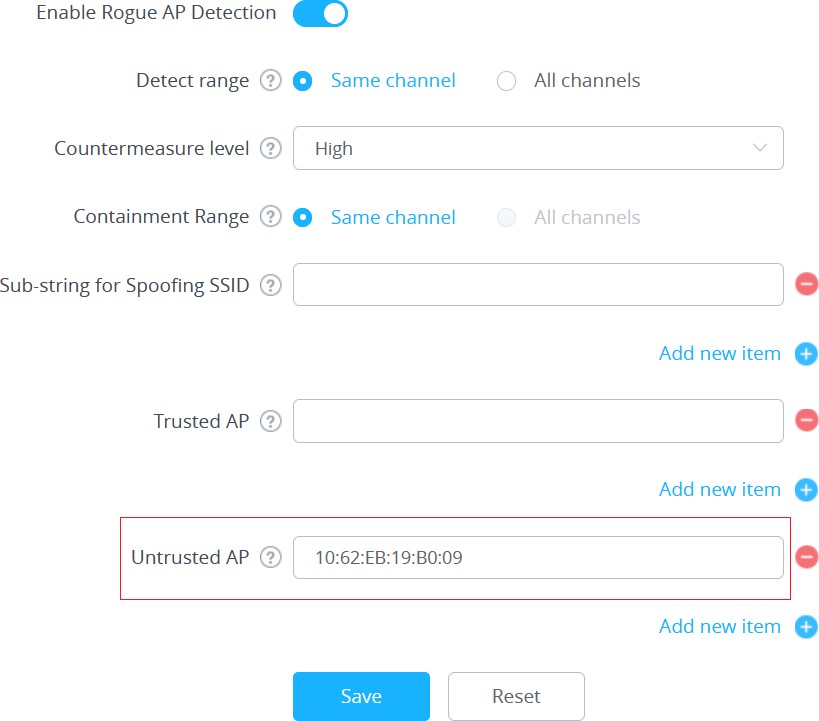
You can also define an AP as Untrusted from the “Actions” tab located under “Security” → “Rogue AP” → “Detected” by clicking the icon as shown in below screenshot.
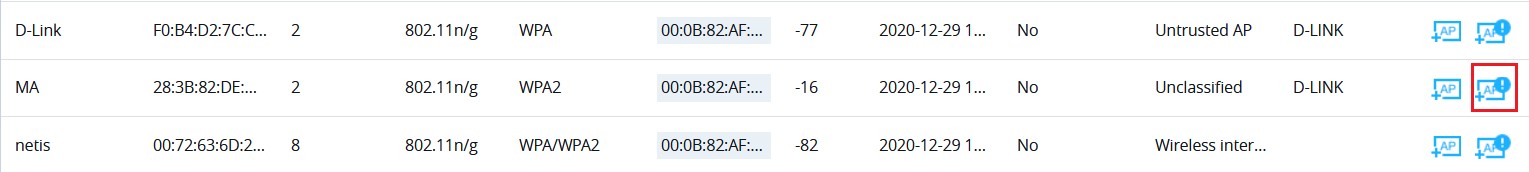
Note: If an AP is defined as Untrusted AP, countermeasures will be executed on it when countermeasure is enabled.
DETECTED ROGUE ACCESS POINTS
The “Detected” page shows all the SSIDs within the Wi-Fi coverage of the GWN76xx, including the APs that have been set as Trusted or Untrusted.
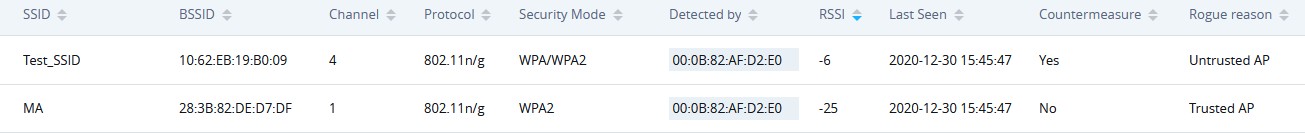
When the GWN76xx AP detects the signal of another neighboring wireless access point, it compares the characteristics of the AP to a list of configured Trusted or Untrusted APs. If the discovered access point does not match any trusted or untrusted AP, the GWN76xx reports the device as a “Wireless interference” under the web GUI “Detected” page as shown in below screenshot.
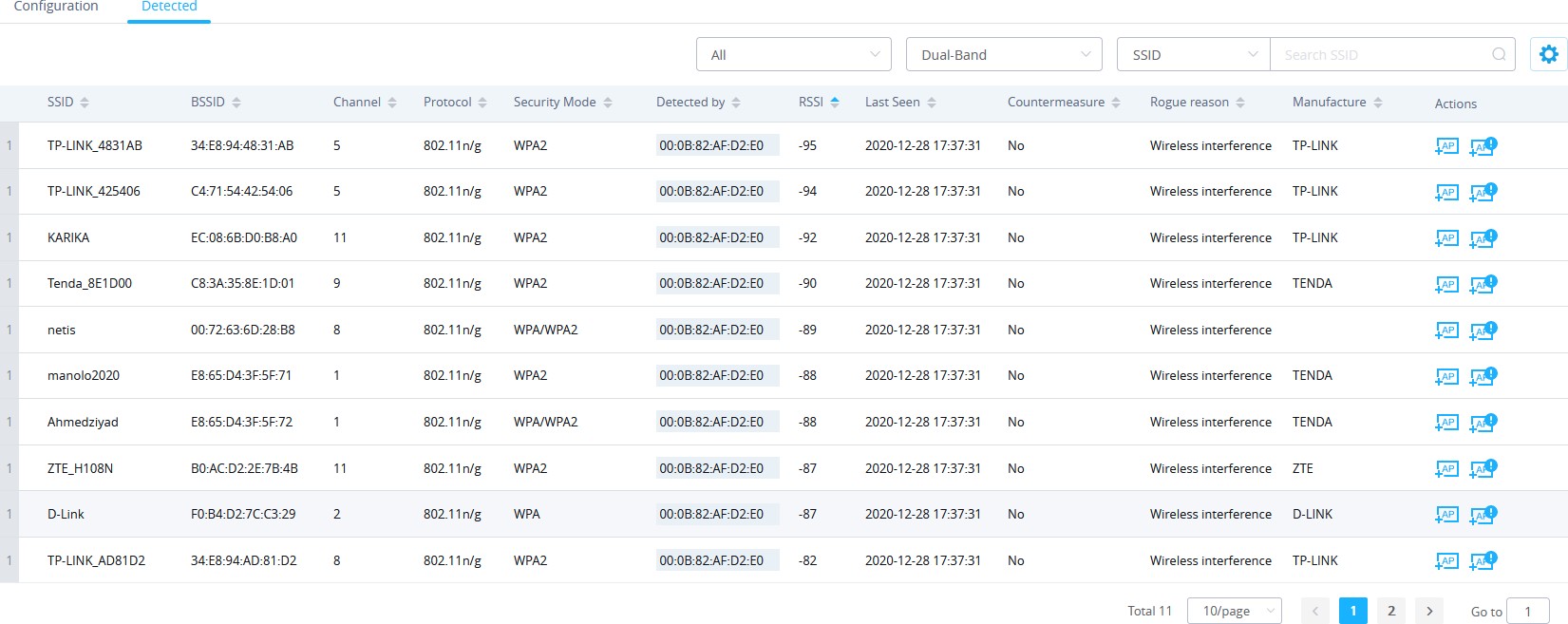
Note: An Access point is considered to be an interfering AP if it is seen in the RF environment but is not connected to the wired network. While the interfering AP can potentially cause RF interference, it is not considered a direct security threat since it is not connected to the wired network. However, an interfering AP may be reclassified as a rogue AP.
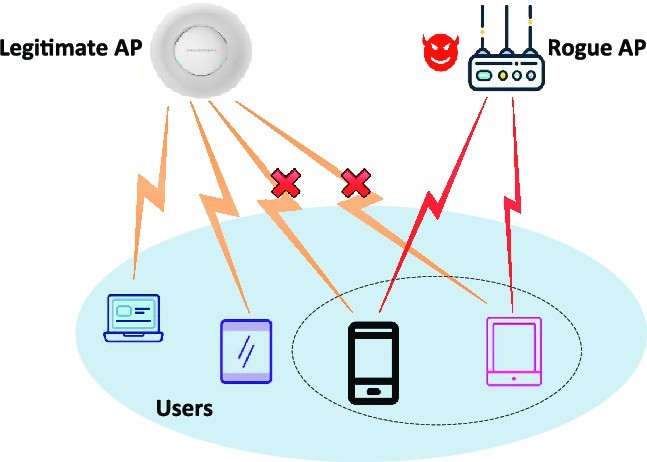
ROGUE AP CONTAINMENT
When the countermeasure option is enabled and a client tries to associate with an untrusted or spoofing SSID access point, The GWN76xx AP automatically begins sending broadcast de-authentication messages spoofing the rogue’s BSSID (MAC) to prevent wireless clients from connecting to that malicious rogue AP.
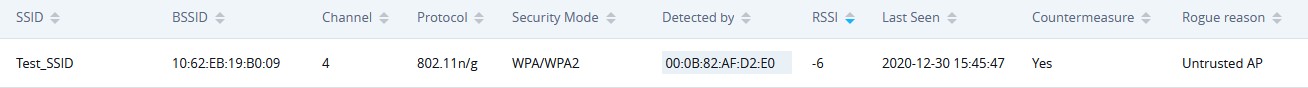
When a countermeasure is taken against a rogue Untrusted AP, It will be displayed in “Detected” page under Security” → “Rogue AP” as shown in below screenshot.
SUPPORTED DEVICES
Following table shows Grandstream Wi-Fi Access Points supporting the Rogue AP Detection feature:
Model | Supported | Firmware |
GWN7615 | Yes | 1.0.19.9 or higher |
GWN7600 / GWN7600LR | Yes | 1.0.19.9 or higher |
GWN7605 / GWN7605LR | Yes | 1.0.19.9 or higher |
GWN7630 / GWN7630LR | Yes | 1.0.19.9 or higher |
Note: This feature is not supported in GWN7610 and GWN7602.